
UNDERSTANDING THREATS
Recognizing and Avoiding Phishing Scams
What is Phishing
How it Works
Types of Attacks
How to Detect it
Solutions

What is Phishing?
Phishing attacks attempt to steal a victim’s identity or to obtain access to sensitive data. They can be carried out through various channels, including email, social media, messaging apps, and phone calls.
Attackers often use social engineering tactics to persuade the victim to take a specific action, such as clicking on a link or downloading a file, prompting them to give personal information.
It is important to be vigilant and cautious when receiving unsolicited messages or requests for personal information, and to always verify the authenticity of the sender or website before providing any sensitive information.
How does phishing work?

The attacker sends an email to the victim.

The victim clicks on the email and is taken to the phishing website.

The attacker collects the victim’s credentials.

The attacker uses the
credentials to access
a website.
Types of Phishing Attacks
Spear Phishing
Directed at specific individuals or groups. Attackers use personal information, such as a name or job title, to make the email appear more convincing.
Clone Phishing
This is a type of phishing attack that involves creating a fake copy of a legitimate email or website. The attacker then replaces links or attachments with malicious ones.
Whaling
This is a type of spear phishing attack that is targeted at high-level executives or other important individuals within an organization.
Smishing
This is a type of phishing attack that is carried out through SMS or text messages. The attacker may request that the recipient clicks on a link or enters personal information.
Vishing
A type of attack carried out through voice calls. The attacker may impersonate a legitimate organization, such as a bank or government agency, and request that the recipient provides personal information.
Pharming
This is an online scam similar to phishing, where a website’s traffic is manipulated, and confidential information is stolen. It is the criminal act of producing a fake website and then redirecting users to it.
How to Detect Phishing
Detecting phishing requires a combination of vigilance and awareness. Common signs of a phishing attempt include suspicious links, requests for personal information, and urgent or threatening language. Ask yourself the following questions when you are about to open a message…
Urgency
If an email pushes you to take immediate action, approach it with skepticism.
Email Address
Spammers will create email addresses that are similar to legitimate ones, but contain slight variations.
Grammar
Phishing emails are often characterized by poor spelling and grammar.
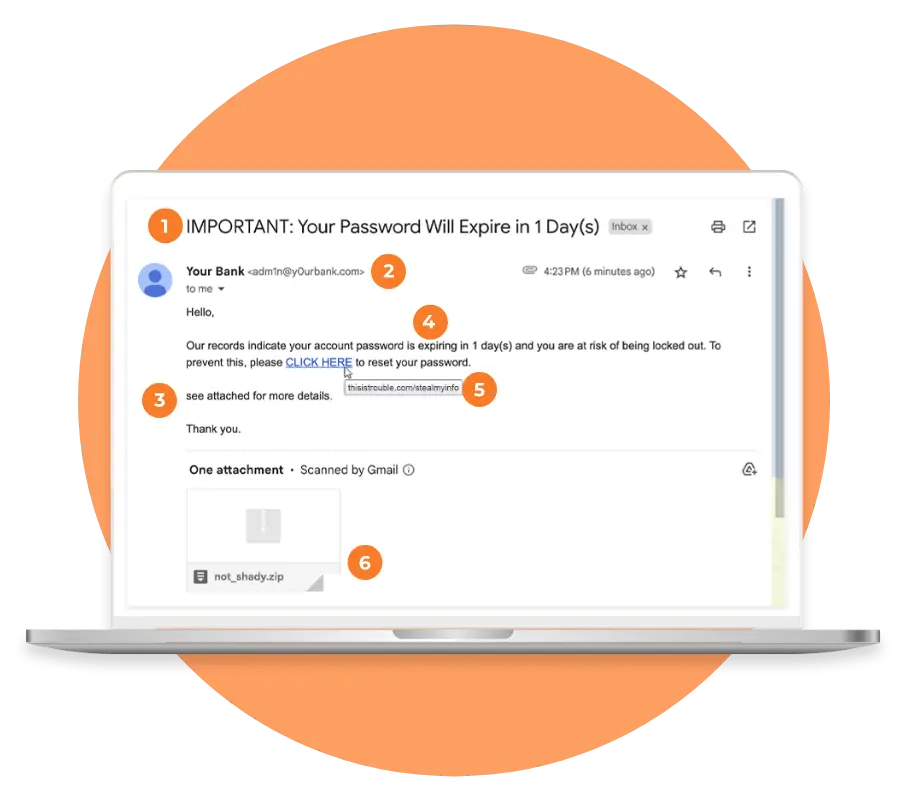
Data
If you’re asked for personal information, providing it could put you at risk of identity theft or financial fraud.
Links
Hover your cursor over any links to check the destination before clicking. Don’t click if the domain names is unfamiliar.
Attachments
If you didn’t expect to receive a file, use caution before opening the attachment.
PHISHING BUNDLE
Solutions to Secure
To safeguard your organization, our products proactively block phishing attacks before they even reach your inbox.
with a Port53 Security Expert
Discuss Phishing Protection with a Port53 Security Expert
Learn More
Redefining Network Protection: Cisco Hypershield
Traditional firewalls are no longer sufficient to protect against the sophisticated threats modern organizations face. Recognizing this, Cisco has introduced Cisco Hypershield, a groundbreaking security solution that promises to revolutionize network protection. With...
How to Protect Against Ransomware
How to Protect Against Ransomware Ransomware continues to plague businesses, with this past March breaking records: “March 2023 was the most prolific month recorded by cybersecurity analysts in recent years, measuring 459 attacks, an increase of 91% from the previous...
Steps for a Secure Summer Online
As the weather gets warmer and the flowers start to bloom, it's a good time to consider giving your cybersecurity habits a "summer cleaning" as well. With digital threats and attacks becoming increasingly sophisticated, it's more important than ever to proactively...








