
BLOCK PHISHING
Proactive Phishing Protection
Stay ahead of phishing attacks with enterprise-grade security controls.
BLOCK PHISHING
Proactive Phishing Protection
Stay ahead of phishing attacks with enterprise-grade security controls.

Don’t Become a Statistic

of cyber attacks start with a phishing email

for someone to fall victim to a phishing scam
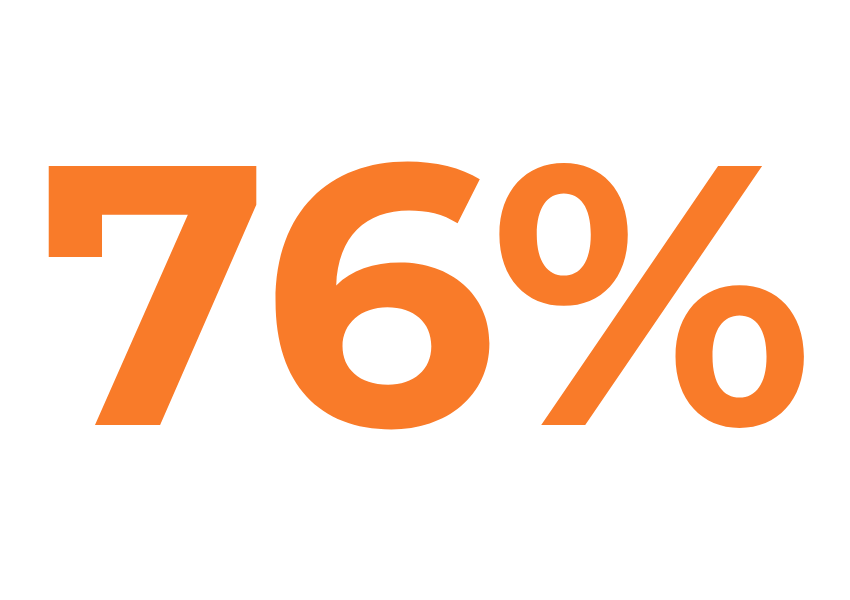
of organizations fell victim to phishing attacks in the last year
Are you at Risk?
Take our Phishing
Assessment today!
What Can You Do?
One of the fastest ways to protect against phishing is to implement Multi-Factor Authentication (MFA).
Microsoft found that MFA alone can block over 99.9% of account-compromise attacks.
Cisco Duo verifies the identity of your users with two-factor authentication and the security health of their devices before they connect to your applications.


Trusted Users
Duo verifies the identity of users and protects against breaches, verifying trust in multiple ways before granting access.

Trusted Devices
With Duo, device trust becomes a part of the authentication workflow providing in-depth visibility across all devices.

Trusted Locations
By leveraging contextual information, Duo verifies the user’s physical location before granting access.
Your Workplace is Vulnerable
Phishing attacks have serious consequences. There are several vulnerabilities that workplaces face, including…
Phishing Attacks Have
Serious Consequences
Phishing Attacks Have Serious Consequences
In order to protect your business, you must protect your data. It’s essential to take precautions such as educating oneself and employees on phishing attacks, using anti-phishing software, and implementing multi-factor authentication.
Data Breaches
Identity Theft
Reputation Damage
Financial Loss

How is Port53 in a
Position to Help?
How is Port53 in a Position to Help?
We provide enterprise-grade protection that is easy to deploy, simple to manage, and highly effective, allowing you to focus on serving your customers without worrying about cybersecurity threats.
Solutions to Secure
Discuss Phishing Protection with a Port53 Security Expert
with a Port53 Security Expert
Learn More
Redefining Network Protection: Cisco Hypershield
Traditional firewalls are no longer sufficient to protect against the sophisticated threats modern organizations face. Recognizing this, Cisco has introduced Cisco Hypershield, a groundbreaking security solution that promises to revolutionize network protection. With...
How to Protect Against Ransomware
How to Protect Against Ransomware Ransomware continues to plague businesses, with this past March breaking records: “March 2023 was the most prolific month recorded by cybersecurity analysts in recent years, measuring 459 attacks, an increase of 91% from the previous...
Steps for a Secure Summer Online
As the weather gets warmer and the flowers start to bloom, it's a good time to consider giving your cybersecurity habits a "summer cleaning" as well. With digital threats and attacks becoming increasingly sophisticated, it's more important than ever to proactively...












