Penetration Testing & Vulnerability Management
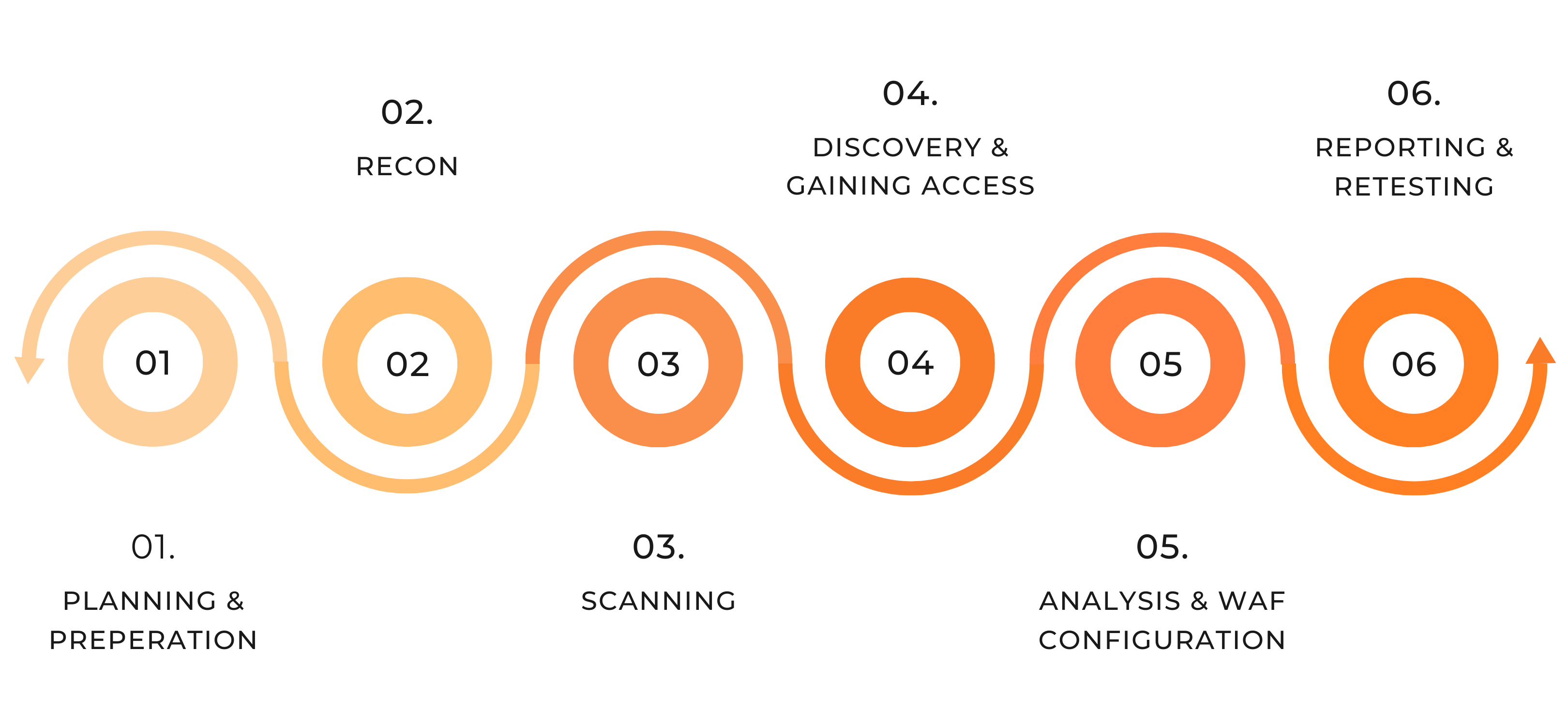
Penetration Testing Stages
Vulnerability Coverage. Actionable Report. Quick Remediation.
Historically, penetration testing has been manual and labor intensive, requiring individuals to launch ad-hoc attacks against their organization to find vulnerabilities. Because of the extent of time and resources this process consumed, it came with a hefty price tag and a heavy lift.
Any company with a robust, proactive security posture needs to have an understanding of their vulnerabilities and the changing threat landscape. Port53 has developed a means to leverage the power of the cloud to give organizations of all sizes access to enterprise level testing at a per IP price point.
Get on Bill’s calendar to discuss Penetration Testing as part of an overall program that optimizes your security outcomes.
Types of Network Penetration Testing
External Pen Testing
Black Box
This test is carried out with no knowledge about the organization’s network. The tester uses penetration testing tools or social engineering techniques to show exactly what a potential hacker can see in your network.
Internal Pen Testing
White Box
Testers have complete knowledge of what they are looking for and conduct an internal penetration test to see what risks may arise from within the network. This is done by connecting to the LAN and exploring potential vulnerabilities.
Segmentation Testing
Gray Box
The tester is given access to the internal network in order to simulate an employee and assess internal threats within the company. Segmentation testing ensures that communication between networks is restricted.
