Below, we examine the new Model 2.0 version of CMMC from three perspectives:
- Why did the DOD make the changes?
- What are the benefits?
- What are the downsides?
Why did the DOD make the changes?
Model 1.0 of the Cyber Maturity Model Certification (CMMC) framework was a big ask for small businesses (those with annual revenues below $100 million). Small businesses are estimated to be more than 99% of the companies in the Defense Industrial Base (DIB). Visually, the skew toward small businesses in the DIB is dramatic.
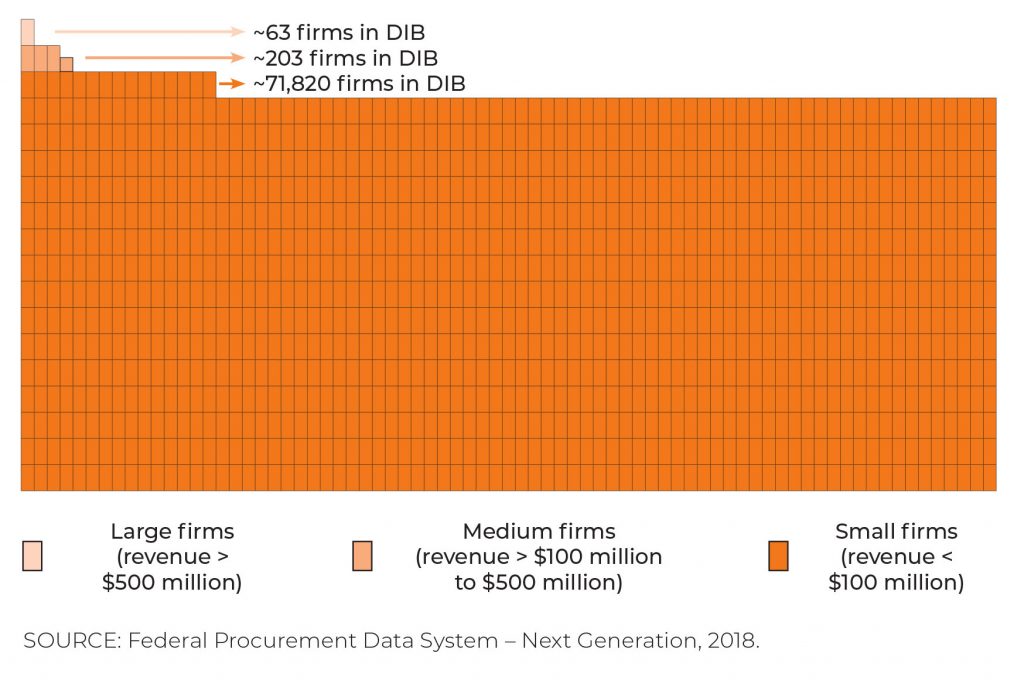
Compliance with Model 1.0 required meeting all Maturity Level 3 (ML-3) controls when handling Controlled Unclassified Information (CUI). The definition of CUI has long been considered murky, compounding the difficulties for smaller firms in trying to maintain compliance. Such businesses also faced significant remediation costs, and had to pay some $50,000 for audits every three years.
The changes described below were mostly directed at small businesses in the DIB. The 266 medium and large DIB firms did not encounter the same issues with Model 1.0.
What are the benefits?
Under Model 2.0, companies that only access Federal Contract Information (FCI) – the least sensitive type of non-public information in the DIB – need only comply with the 17 controls found in the original ML-1 in Model 1.0.
Companies accessing CUI under the new model must comply with the newly defined ML-2. The old ML-2 has been eliminated, and the old ML-3 is now ML-2 under Model 2.0. Most importantly, ML-2 in Model 2.0 calls for precise compliance with NIST 800-171. Anything added by the DOD as part of Model 1.0 that went beyond NIST 800-171 has been removed. The DOD made the decision to not assume the role of developer, manager and enhancer of a security framework. Instead, the department handed this responsibility over to NIST.
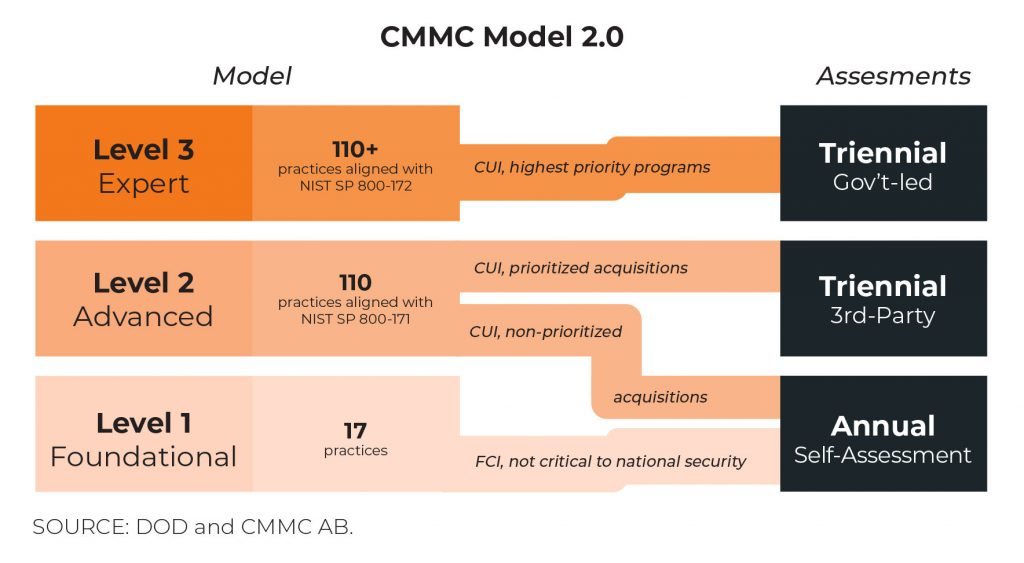
So far, we have covered framework changes. But perhaps the greatest benefit to small businesses in Model 2.0 is the way companies are required to document compliance. Under a new classification of acquisitions (contracts), only prioritized acquisitions will call for the company to perform a full assessment audit every three years, as under Model 1.0. But non-prioritized acquisitions, only require annual self-attestations of compliance. The DOD and Contracting Officer at the prime will be making this determination.
And POA&Ms (Plan of Actions and Milestones) have made a return as stopgaps for compliance in lower-priority programs. Rather than having to demonstrate consistent, ongoing compliance with every control, a responding company must meet a minimum score, as with the current interim rule. They will then commit to closing the gaps within 180 days, through agreed POA&Ms.
Companies should note that for the highest priority programs (requiring Level 3 compliance, or “Expert” in the above diagram), POA&Ms will not be available.
What are the downsides?
CMMC Model 1.0 was a bold, next-generation security framework. The control side of NIST 800-171 had been extended, with 20 additional controls, and a second dimension of process maturity was added. As I worked with small businesses implementing Model 1.0, these extensions provided concisely defined waypoints for developing roadmaps for security implementation over multiple years. And I am implementing Model 1.0 with both DOD and commercial clients.
Also, ML-2 in Model 1.0 provided additional guardrails to phase a client’s investment and effort as they continually improved their security posture.
So, perhaps the greatest downside is having to bid farewell to a framework that was friendly to smaller DIB businesses. I will continue to recommend CMMC Model 1.0 to smaller commercial businesses not driven by regulations around a specific framework. This will include the 20 additional controls and added process-maturity dimension. These extensions are all about improving security posture and reducing risk. At Port53 we call this “securing the business”.
Learn More
To learn more about CMMC check out our other blog posts below:
The Brilliance of CMMC for the Medium to Small Businesses in the Defense Supply Chain Part 1
The Brilliance of CMMC for the Medium to Small Businesses in the Defense Supply Chain Part 2


Recent Comments