When to Automate Security Workloads
Automating security workloads is essential because sometimes, enough is enough. Security practitioners were never meant to manage the weight of millions of new threats with manual tools and practices alone. New methods are needed.
Security tools are designed to keep pace with current threats in the industry. So, when threats go on auto-pilot, security workloads do, too. For those teams still struggling to find the line, here are five ways to know when it’s time for your organization to automate security workloads.
1. When Performing Vulnerability Assessments and Penetration Tests
It used to be enough to do a penetration test once every year – maybe twice. But now, the rate of change and the sheer volume of new threats make this type of proactive protection necessary on a regular basis.
Offensive security measures like penetration testing are not a one-and-done. When a company takes on a new SaaS solution, web application, IoT device or OS software, a new risk is introduced. For modern enterprises to keep up with the rate of change, they need to be consistently checking for vulnerabilities and patching them when found.
Automating this effort through automated vulnerability scanning and pen testing solutions can help organizations stay on top of new risks as they come into the organization.
2. When Securing Access Management in the Cloud
Securing access across a myriad of environments can be tricky. Enterprises today must worry about hybrid, cloud and remote workspaces and employees logging in anytime from anywhere. Gone are the days of simple office-based network management where anyone on the corporate WiFi was covered.
Customizing secure, Multi-Factor Authentication (MFA) across all environments can be a daunting task as enterprises continue to scale digitally. An automated access management solution like Duo Security MFA, OneLogin, or Cisco Cloudlock can make securing an enterprise’s worldwide users easy, no matter when or where they authenticate.
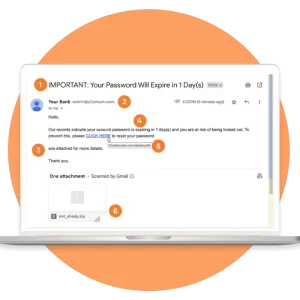
3. When Dealing With Thousands of Emails
Phishing is still one of the top three ways a hacker will breach an organization, per this year’s Verizon Data Breach Investigations Report. Various industry reports note that there are 3.4 billion spam emails sent every day, and nine in ten organizations have fallen victim to phishing attacks in 2022.
The rate of sending malicious emails looks even worse when pitted against the stretched resources of many organizations still struggling under the cyber talent crisis. Automating email security, especially in the cloud, is critical to combating the sheer volume of potential spam companies face daily.
4. When Securing Your Endpoints
The more devices added to a network, the more endpoints. Endpoints are where the rubber hits the road, and users interact with a company’s internal network systems. These can be mobile devices, laptops, virtual machines and even printers.
A Ponemon survey noted that the average company has over 135,000 endpoints to protect. That represents a 17,900 percent increase over similar figures pre-pandemic.
The bottom line is that there are too many for a simple SOC to protect. Automated endpoint security solutions are a necessary tool for doing business in a post-pandemic digital landscape.
5. When Overwhelmed With Incident Detection and Response
The final, and perhaps most logical, result of an overwhelming amount of new systems, users, emails, and endpoints is an overwhelming amount of incidents on the loose.
It’s vital to have solutions at the door: automated tools to spot misconfigurations and secure authentication, email, and endpoints. However, some will inevitably slip through – even thousands. As emerging exploits evade traditional signature-based techniques, new tools are needed to catch them.
These automated detection and response solutions, known by the -DR denominator, use machine learning and artificial intelligence to spot malicious behaviour patterns, enabling even small SMB organizations to catch sophisticated new exploits at scale. When partnered with a managed Security Operations Center (SOC), the benefit is optimized, and teams can save on tools and talent.
Automation: Not Nice, Necessary
Why automate? Because companies need help to handle increased risk.
What increases risk? The amount of new technologies organizations ingest every quarter, the number of IoT devices they take on, the amount of new code that comes from OS code bases, the volume of new services and software programs, and the number of third-party vendors, partners, and suppliers all add to the load. On top of that, these systems are all plumbed by eager attackers looking for vulnerabilities and plying their craft with exploits.
The weight of the combined security workload is too much for companies to handle with manual efforts alone. As automated platforms create more data, automated solutions must analyze and secure it. As attackers use automation to force-multiply, so must we.
Learn more about how Port53 can help you automate your security workloads today.
Check out our Customer Platform

Ransomware Doesn’t Pull Punches for SMBs: How Small Businesses Can Defend Like an Enterprise
Ransomware is getting sneakier, more brazen and easier to proliferate. Small and mid-sized enterprises may think they’re off the hook, but the tides have changed.


Recent Comments