
UNDERSTANDING SECURITY
What is Cybersecurity?
Cybersecurity boils down to protecting your digital assets, by whatever technological means necessary. A more in-depth explanation would be the practice of deploying people, policies, processes and technologies to protect organizations, their critical systems and sensitive information from digital attacks. Let’s give you the basics so you can understand how to build out a cybersecurity model for your organization.
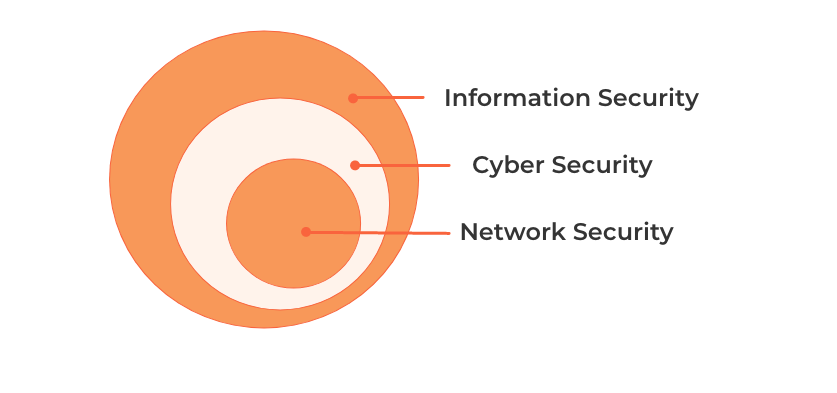
To understand what cybersecurity is, you must first understand what it is not. Cybersecurity lies within Information security, and encompasses Network security.
Common Miconceptions
Before we begin, let’s bust some common cybersecurity misconceptions.
“Cybercriminals are hooded hackers from some foreign country.” Nope. Quite often they’re insiders who know your network.
“We have a list of all possible cyberthreats.” Not even close. The threat of new ransomware models was a top concern among executives last year, reports Gartner.
“My industry isn’t at risk.” Geopolitical tensions and increasingly lucrative payout schemes have prompted attacks on healthcare, school districts, critical infrastructure and retail. Any organization online is, by default, at risk.
Common Cyber Threats
There are many, many more but these are some of the most common low-hanging-fruit attacks companies typically face.

Ransomware is the act of stealing and encrypting a victim’s data, then demanding
payment for the data back and a decryption key. This industry went from nuisance-level pop-ups demanding several thousand dollars to large-scale campaigns
demanding up to $50 million.

Phishing is when a cybercriminal sends you a fake email that diverts you to a bad site where you’re tricked into giving away information and is how 90% of data breaches occur, according to Cisco’s 2021 Cybersecurity Threat Trends Report.

Password-related account compromises happen when we use unsafe passwords that hackers can easily crack: too short, too shared or too reused.

APTs. Advanced Persistent Threats (APTs) are highly sophisticated, nation-state level attacks that lay low on a victim’s system for months at a time, secretly siphoning out data.
Cybersecurity Frameworks and Regulations
t’s hard to hit the target if you don’t know what you’re aiming for. A cybersecurity framework gives you a set of metrics, rules or principles against which to build your security stack, and there are several industry-standard ones to follow. Here are three you might recognize:
If you’re not sure where to start, a cybersecurity performance assessment company like TrustMap can help you see where you stand.

Learn more about TrustMAPP
TrustMAPP delivers continuous Cybersecurity Performance Management, giving CISOs a real-time view of the effectiveness of their cybersecurity program. Book a call and we’ll tell you more about it.
Best Practices
If we’re all to return to the workplace, continue working remotely, or just function in today’s online-everything cyber space, a few ground rules need to be observed in order to do it safely.
Policy
Data Backups
Zero-Trust
Cyber Hygiene
Have an enforceable cybersecurity policy.
Protect sensitive data by monitoring outside access, watching privileged users and performing backups.
Protect sensitive data by monitoring outside access, watching privileged users and performing backups.
In addition to basic firewall and antivirus controls, it is crucial to cover connection, identity, email, and user-training in order to stay healthy.
Security Solutions
So now for the overview. Here is a (non-exhaustive) list of security types that most organizations look to invest in:
Network Security
Network Security is anything that protects your underlying network infrastructure and everything that’s on it. With Meraki MX you get a ready-to-go set of features that includes firewalls, malware protection, content filtering, a self-healing VPN and more
Cloud Security
Not all cloud providers provide cloud security, so protecting cloud-based assets ultimately falls on the asset owner – you. Port53 provides a managed cloud-delivered solution that relies on Cisco Umbrella and is easy to deploy, integrate and scale.
End User Analytics
Spot anomalous behaviors at your endpoints instead of just searching for malicious code (which hackers are now disguising). Port53 offers AI-driven Secure Analytics as part of our SOC-aaS, protecting your network with Extended Detection and Response (XDR).
Identity Security
To ensure the confidentiality and integrity of your data, you have to make sure that everyone who has access to it is who they say they are. Verify user authenticity with automated tools like Duo, OneLogin and CloudLock.
Email Security
Email security is a must as that is how the vast majority of phishing schemes get through, sending malicious attachments and gleaning valuable data. Leverage the power of modern APIs with Cisco Secure Email and Cisco Mailbox Defense.
End Point
Endpoints are any physical device directly connected to your network such as mobile phones, laptops, servers, and VMs, and they are a major point of attack. Secure your endpoint devices with Cisco Secure Endpoint and use the power of big data to block and respond to threats.
Umbrella Security
Umbrella Security pulls it all together by preventing malicious sources at the DNS layer and presenting a first line of defense against internet-based attacks. And, Umbrella rolls out the same security to remote workers without the need of a VPN.

We’re Here to Help
Port53 is an award-winning cybersecurity consultancy that can help you integrate enterprise-grade solutions into your security stack, no matter where you are on the cyber maturity model. Don’t even know what that is? No problem. We can help you find out, then suggest solutions, benchmark progress and bring our experience to the table as we move with you towards full cybersecurity resilience. Learn more about Port53’s cyber services.















