Attack Surface
Management
Take the guesswork out of understanding and protecting your organization’s digital footprint.
What is ASM?
Attack Surface Management (ASM) is the continuous monitoring, discovery, inventory, classification and prioritization of sensitive external assets within an IT organization’s infrastructure.
Why is it important?
ASM helps to prevent and mitigate risks from vulnerable and outdated software, human mistakes and omissions such as phishing and data leaks, targeted cyber attacks, unknown open-source software, and more.
RISK ASSESSMENT
What you can do
Port53 has partnered with Censys, the leader in Attack Surface Management, to offer a free no obligation risk assessment. Get insight into your critical infrastructure by uncovering unknown cloud and internet facing assets.

How the Complementary Assessment Works
Port53 has partnered with Censys, the leader in Attack Surface Management, to offer a complementary risk assessment. Get insight into your critical infrastructure by uncovering unknown cloud and internet facing assets.

1:1 with Cloud
Security Expert
A Port53 sales expert will walk you through the Risk Assessment program and answer your questions to ensure you’re set up for success!

Key Risk
Findings Report
A detailed summary of your security risks and an executive presentation with a Port53 and Censys expert who will review the downloadable report findings with you.

Full Access to
the Platform
Get full access to the Censys platform for 15 days and immediately get actionable insights and remediation recommendations for your most critical security risks.
Censys.io Assessment
To receive your complementary Censys.io assessment, please provide the following information.
ABOUT CENSYS
What Censys Does
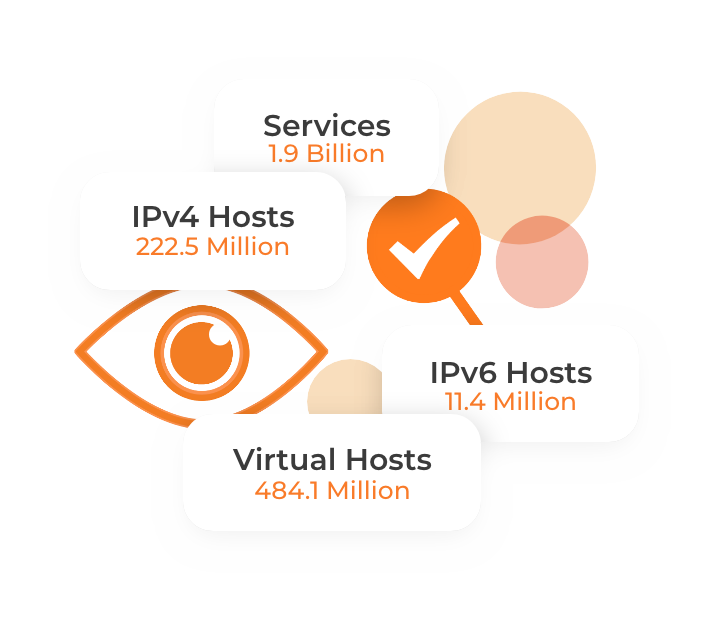
Censys scans the entire internet from three different, global scan perspectives amassing:

Over 240 million IP addresses

1.1 Billion services discovered on over 3,500 ports

Over 8.4 Billion certificates and associated info into the UIDS
Censys helps make the internet a secure place for everyone. Stay one step ahead of risk by showing you threats before they become complications and delivering tools and insights to mitigate risks. From the corporate network to the cloud and beyond, a secure internet starts with Censys.
ABOUT CENSYS
Censys ASM allowers defenders to…

Discover Unknown Assets
The foundation of Attack Surface Management lies in the initial and ongoing discovery of internet-facing assets and risks. To find unknown assets, Censys ASM continuously trawls internet data sources such as Certificate Transparency logs, passive DNS sinks, and internet scans to uncover assets that you own. Censys discovers unknown and unmanaged internet-facing assets — including services, hosts, websites, storage buckets, and cloud accounts — across all clouds and networks in real time.
Prioritize and Remediate Risks
There are too many factors to your data and assets to keep it all straight, up-to-date, and accounted for. Mismanaged cloud configurations. Expiring certificates. Aging and vulnerable properties. Through our industry-unmatched algorithmic discovery and automated attribution, we’re always on. Always seeing. Always helping.
Manage Merger and Acquisitions Activity
Mergers and acquisitions (M&A) provide growth-oriented strategies to rapidly expand offerings, customer base, and bottom line. However, coming together can be challenging from a systems, cultural, and technology point of view. Before the ink is dry, the risks to your organization may have grown exponentially. We’re here to help take the questions out of this new, exciting reality.
Identify Mismanaged Cloud Services
The cloud presents endless organizational advantages. And endless opportunities for open doors. Our scans of the internet go wider and deeper than anyone to find the potential misconfigurations and help you shore them up. Because we all love to sleep at night.
Maintain Organizational Compliance
Exposed data can easily bring your organization out of compliance. Censys checks all of your Internet assets for security weaknesses that could bring your organization out of compliance.
Ready to get started?
Meet with one of our security experts to discuss your needs.
