The Importance of Cyber and Network Security
Cybersecurity is referred to as the whole, and network security is one very important part.
A network is a grouping of machines (computers, devices, etc.) that send data to one another. They are digitally connected, share communication protocols, and access assets from the same network nodes. Network security includes protocols that secure the transfer of information between them, such as firewalls, DDoS authentication, and access control platforms like MFA.
Cybersecurity is the overall protection of any virtual exchange and any digital asset within your enterprise as a whole. This covers what happens on media devices, mobile phones, the IoT, in APIs, across the software supply chain, and in the cloud.
A modern enterprise relies on strong foundations in both to combat modern-day threats. You cannot leave one side of the store unattended. Along with that goes physical security elements (like smart cams in the server rooms), but we won’t go into depth on that here. The right security solution can offload the burden of all three by centrally managing both cyber and network (and physical) security from one location, hosting it in the cloud, and reducing overhead to only one IT staff member to manage the whole thing.
You might think they’re two of the same thing, but they’re not: Cybersecurity and network security are two compatible sides of the same coin. Both have to be attended to for complete protection, and in retail, specifically, the stakes are even higher.
What Security Means to Retail
Cashflow is a retail business’s bread and butter, and that cannot continue to grow if it’s diverted. The same goes for all digital systems (which include in-store POS systems): That is why security – of all types – must play an integral role in any retailer’s yearly planning strategy.
Why is retail a target? There are swaths of customer data: Think about every time a customer enters their information to get on the email list, join a discount club, or apply for an in-store credit card. Next, there is an obligation to secure the customers’ interests from engagement (often online), to the transaction (same), to fulfilment (online shipping and more).
Involved are Point of Sale (POS) machines, databases filled with customer contact information, databases containing details on customer loyalty programs, and transaction-centric databases. These contain Personal Identifiable Information (PII) and often grab more than that – say, credit card information – to stay compliant with regulations such as PCI-DSS.
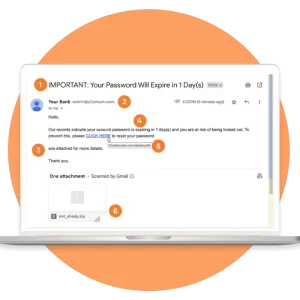
The most common threats facing retail today are social engineering attacks, web application attacks, and system intrusions. Social engineering ploys take many forms, but in retail, they often come in the form of an email advertising an [incredibly good] sale or perhaps a ‘Loyalty Club’ email from ‘the store’ [it’s not]. Web application attacks include SQL injection or cybercriminals plumbing the database through tricky code inserted into forms on a retailer’s website – a feedback form, for example. And system intrusions are everywhere: Anytime someone accesses sensitive information unauthorized – be they through the POS system, an insider attack or any means whatsoever – a system intrusion has been made, and the confidentiality, integrity, or availability of data has been breached.
Feeling a bit overwhelmed?
Get in touch with a Port53 Security Expert and we can help you on the journey to safeguard your retail business and customer data now! We’ll help you fortify your defenses against cyber threats and ensure a thriving, secure future for your enterprise. Don’t wait for an attack to happen—act proactively and stay ahead of potential risks!

How Port53 Can Help
The value of having a managed security services provider (MSSP) in your corner is that all security implementations will be overseen by a relevant expert and all questions answered. In today’s cyber landscape, not only are trained cybersecurity professionals hard to come by, but learning new security systems still takes time and cycles: Time and cycles you no longer have to take if you choose an MSSP like Port53.
Port53 not only provides expert enterprise-level consulting, benchmarking, and strategy alignment, but its dedicated team boasts expertise in a number of cutting-edge security tools. Umbrella acts as a first line of defence against attacks on and off the network, providing you with cloud-hosted coverage. The duo follows up with a detailed internal analysis of all users in all locations and how and why they are accessing company data. Threats come from without and within, and the combination of these two tools provides coverage for both.
Designed to keep up with the digital pace of retailers today, Meraki is a tool that provides a fully cloud-native security experience to retailers. Because of the distributed nature of chain stores, retailers may find themselves juggling network firewalls for each specific location. With often hundreds of stores within a jurisdiction, that amount of oversight can get unwieldy. Meraki is designed to pull all these together under one centrally managed platform. Its cloud-based management can be deployed in minutes (without dedicated staff), and its PCI-compliant cloud architecture not only optimizes security appliances for retail locations but reduces operating costs in the process.
Port53 specializes in helping small to medium sized businesses of all industries meet their security goals. From managed security services to pen-testing and risk assessment, we provide affordable access to enterprise security tools and provide companies with a roadmap of where they are, where they need to be, and what they need to complete their journey to full compliance and security maturity. Click here to learn more.
Check out our Customer Platform
Convergence of Security and Networking
In today’s rapidly evolving IT landscape, the lines between networking and security are becoming increasingly blurred. As companies continue to digitize, the need for seamless integration between these two pillars has never been more apparent. Cisco, a networking...


Recent Comments