
BLOCK PHISHING
Proactive Phishing Protection
Stay ahead of phishing attacks with enterprise-grade security controls.
BLOCK PHISHING
Proactive Phishing Protection
Stay ahead of phishing attacks with enterprise-grade security controls.

Don’t Become a Statistic

of cyber attacks start with a phishing email

for someone to fall victim to a phishing scam
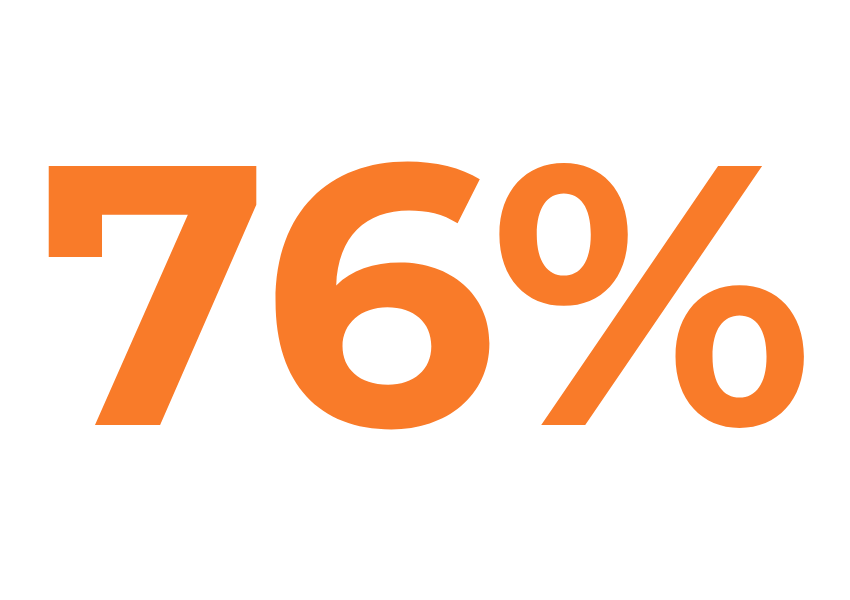
of organizations fell victim to phishing attacks in the last year
Are you at Risk?
Take our Phishing
Assessment today!
What Can You Do?
One of the fastest ways to protect against phishing is to implement Multi-Factor Authentication (MFA).
Microsoft found that MFA alone can block over 99.9% of account-compromise attacks.
Cisco Duo verifies the identity of your users with two-factor authentication and the security health of their devices before they connect to your applications.


Trusted Users
Duo verifies the identity of users and protects against breaches, verifying trust in multiple ways before granting access.

Trusted Devices
With Duo, device trust becomes a part of the authentication workflow providing in-depth visibility across all devices.

Trusted Locations
By leveraging contextual information, Duo verifies the user’s physical location before granting access.
Your Workplace is Vulnerable
Phishing attacks have serious consequences. There are several vulnerabilities that workplaces face, including…
Phishing Attacks Have
Serious Consequences
Phishing Attacks Have Serious Consequences
In order to protect your business, you must protect your data. It’s essential to take precautions such as educating oneself and employees on phishing attacks, using anti-phishing software, and implementing multi-factor authentication.
Data Breaches
Identity Theft
Reputation Damage
Financial Loss

How is Port53 in a
Position to Help?
How is Port53 in a Position to Help?
We provide enterprise-grade protection that is easy to deploy, simple to manage, and highly effective, allowing you to focus on serving your customers without worrying about cybersecurity threats.
Solutions to Secure
Discuss Phishing Protection with a Port53 Security Expert
with a Port53 Security Expert
Learn More
Think you’re not at risk? Think again.
If you have a phone, your company is at risk of a cyberattack. Unfortunately, anyone with a digital presence is at risk these days. If you’re doing anything other than selling lemonade on the corner, your presence in cyberspace will be known as soon as you...
AI Powered Ransomware: Are We Ready?
Ready or not, here it comes. AI is a powerful, potent tool with the ability to learn on its own, get smarter as it goes, and approximate - to an uncanny degree - what a human would do. This is great for cybersecurity. This is terrible for cybercrime. AI-powered...
Security Tips to Stay Safe from Phishing Over the Holidays
While phishing is the threat that never sleeps, it certainly ramps up around the holiday season. It’s almost irresistible - people cramming into online sites to buy, buy, buy, a natural sense of urgency, dopamine clouding our judgment as we excitedly pick out gifts,...












